Thanks to connectivity, innovation is accelerating at an incredible pace, but this is only the beginning. Wireless connectivity has opened up a world of possibilities for every type of product, with surprising ways in which it is used being discovered every day.
The IoT (Internet of Things) refers to a technology that is based on the network connection of every electronic device that surrounds us, as well as measuring their external parameters and automating many of our daily tasks.
In terms of business, IoT devices have ceased to be a small niche market and continue to be one of the most coveted business opportunities currently in existence. The trend of interconnecting all of our devices, along with the fall in the costs of manufacturing these technologies, is providing a huge boost to their uptake.
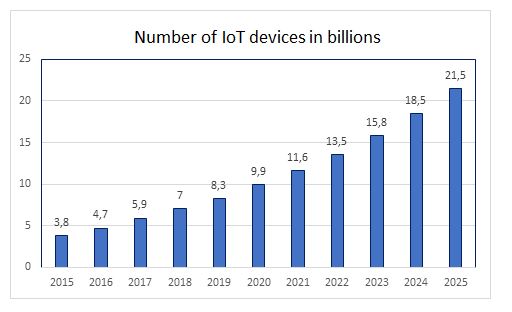
Evolution of the number of IoT devices. Source: IOT Analytics Research 2018
As the graph illustrates, the growth in Internet-connected devices worldwide is following an almost exponential trend, with estimates forecasting that there will be more than 21 billion IoT devices by 2025.
As IoT applications permeate different environments (homes, offices, industrial or public areas...), there will now start to be talk of digital spaces. One of the problems facing this prediction is the ability to manage the enormous amount of data produced by these devices and the information that is handled and processed in such digital spaces.
EDGE COMPUTING
One of the technologies that will come into play with this mass popularisation and acceptance of the IoT, and one that will most benefit from the roll-out of 5G networks, is Edge Computing. In short, this could be defined as the technology that allows the data produced by IoT devices to be processed in the place in which it is generated, rather than transmitting it to an external data centre or cloud platform. This reduces latency and consumes less bandwidth, as well as lightening network traffic and avoiding possible “bottlenecks” that can occur with such platforms and data centres.
As such, the valuable advantage of immediate access to the device data, for its real time analysis and assessment is achieved, - something which has become an essential requirement in many sectors including industry, finance, healthcare and telecommunications. The importance of these changes, as well as the advantages offered by the evolution of the network at new levels, is already a reality.
SECURITY
However, systems are increasingly more exposed to new threats and this places security under the spotlight. The need to securely and efficiently protect the business models that will emerge as IoT and 5G networks gain momentum, presents both opportunities and challenges for communication services suppliers.
IoT success depends on ecosystems integrated into the entire product chain: from device manufacturers, network suppliers, platform providers and application developers to end users. Guaranteeing the integral security of the ecosystem is vital. Decisions are increasingly based on data (such as decisions relating to business, security and health). This is why it is vital to ensure that each device behaves as it should and that its data has not been compromised.
Many experts argue that the security of an Edge Computing infrastructure is even stronger than in a cloud environment, as the less data that is transmitted to a cloud platform or data centre, the less vulnerable that environment will be.
Finally, committing to the use of encryption algorithms to preserve confidentiality, along with protocols that guarantee the integrity of the message, ensuring data reliability and security at all times, are practices that should be instigated. This is because forecasts indicate that the cloud will continue to drive the IT market and a field of essential development over the years to come.
Pablo Clau
Engineer, Smart Systems Department at ELT

